Help Center
Table of Contents
About the portal
Using this portal users can complete self assessements to determine how well their organization manages cyber security risks using established frameworks like the NIST Cyber Security Framework (CSF).
Using the available workbooks, users answer a series of questions to paint a detailed picture of the strengths and weaknesses of the organization's cyber security strategy. Your AI assistant Claudio is available to help with any questions along the way.
Upon completion, the assessment report provides insights about the overall cyber security posture and recommendations to help create an improvement plan.
Assessments can be repeated to track how your organization is improving over time.
Secure your account
Any time you access your account, if MFA has not been set up you will receive a warning message. Click on the link to go to the MFA setup screen.
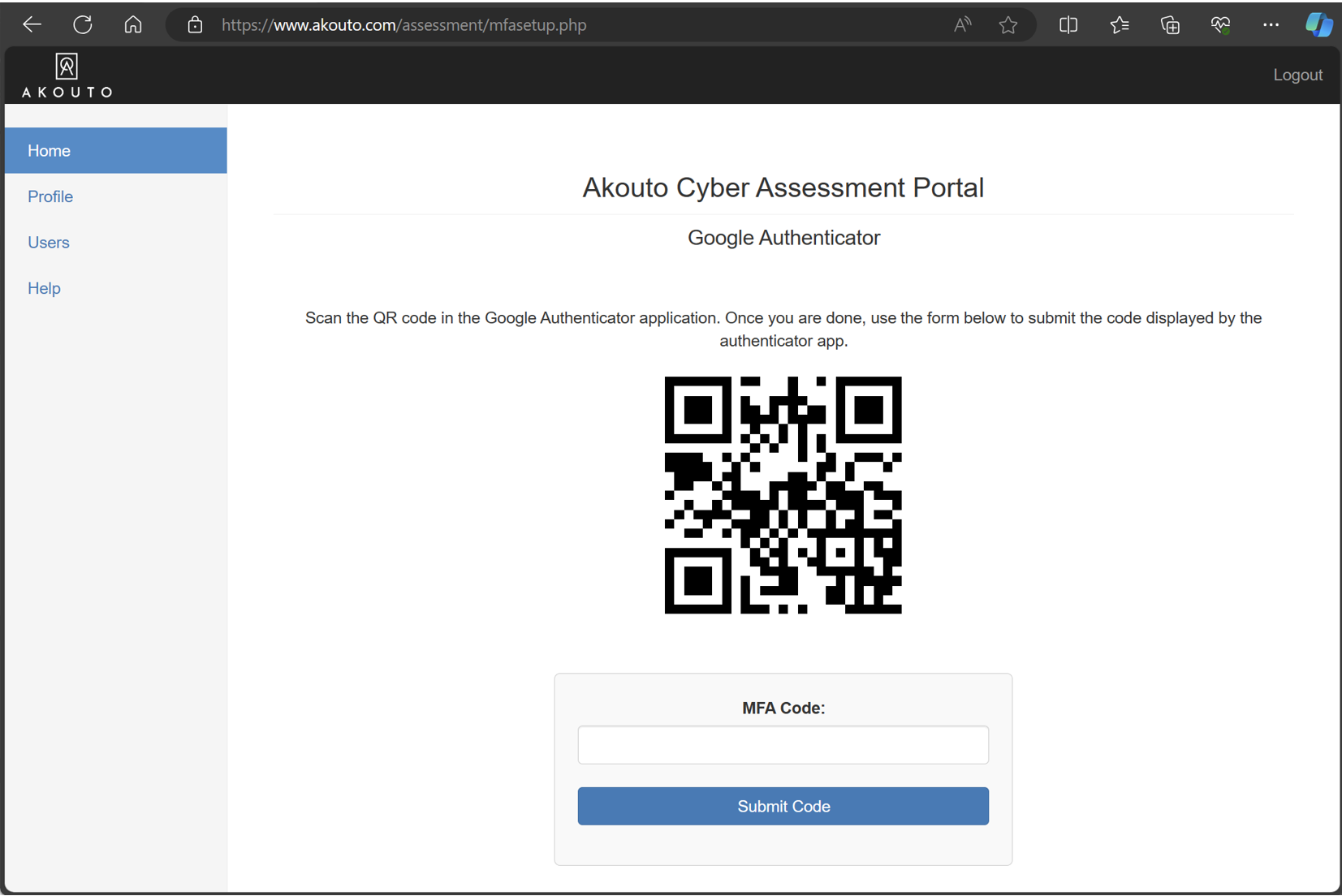
On the MFA setup screen you will be presented with a QR code. Scan it with the Google authenticator app on your phone, enter the code that is displayed on your phone into the MFA Code part of the form and press Submit Code.
Top
Edit your profile
You can make changes to your profile, including changing your password, at any time, by clicking on the Profile link in the left navigation menu.
Top
Add users
If you are the root user for your organization, you can add additional users who are able to access and edit assessments for your organization using the Users link in the left navigation menu.
Top
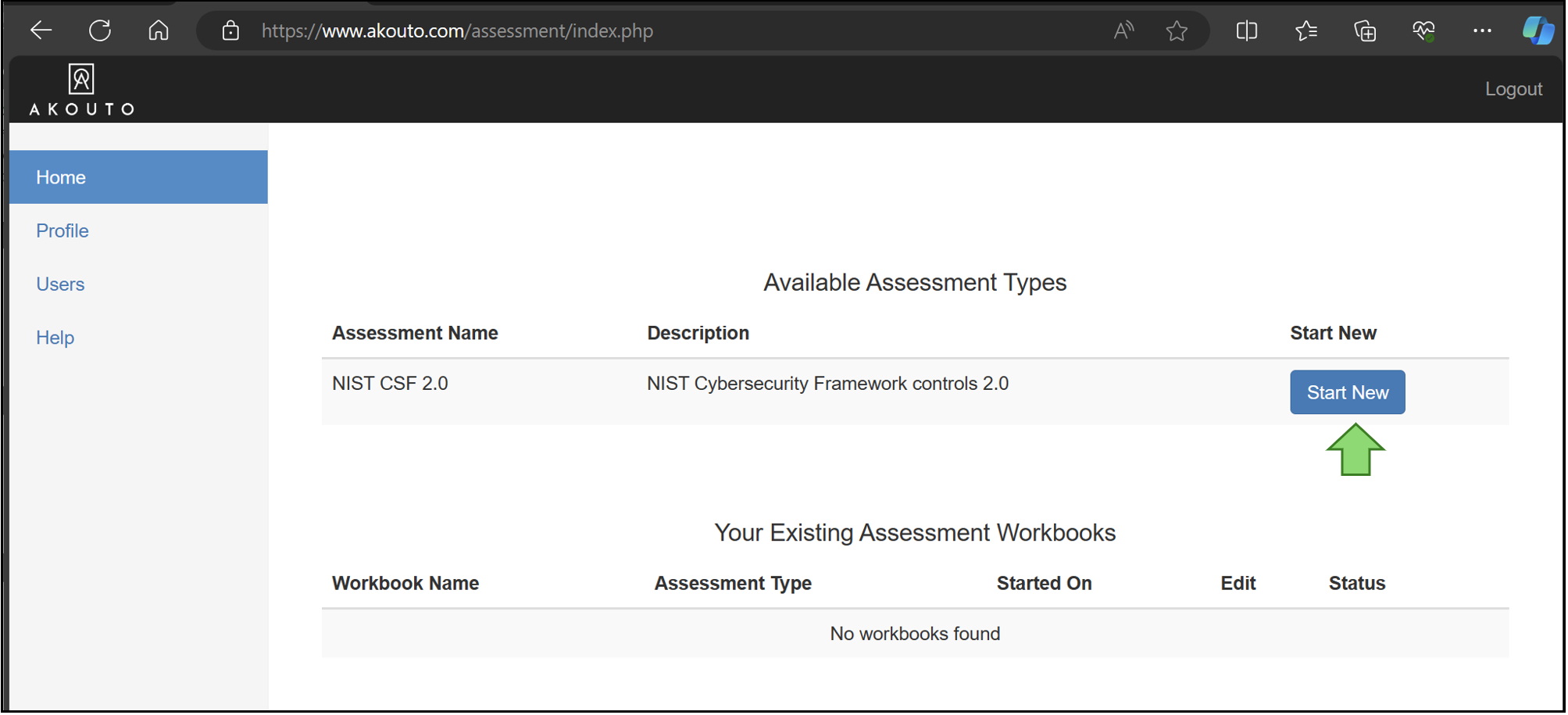
Start an assessment
You can start a new assessment from the main landing page. Click on the Start New button to begin.
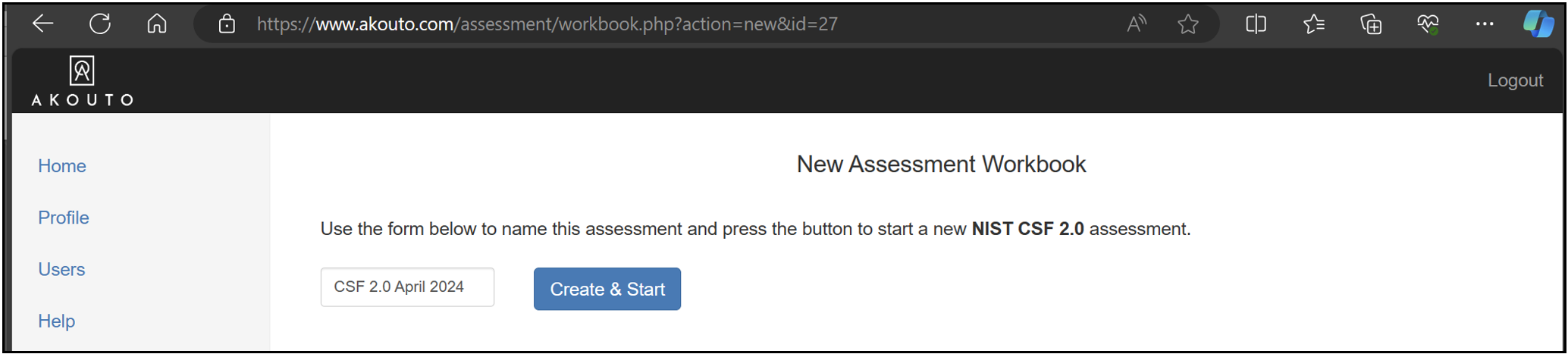
Give the assessment a name and press Create & Start to begin.
Top
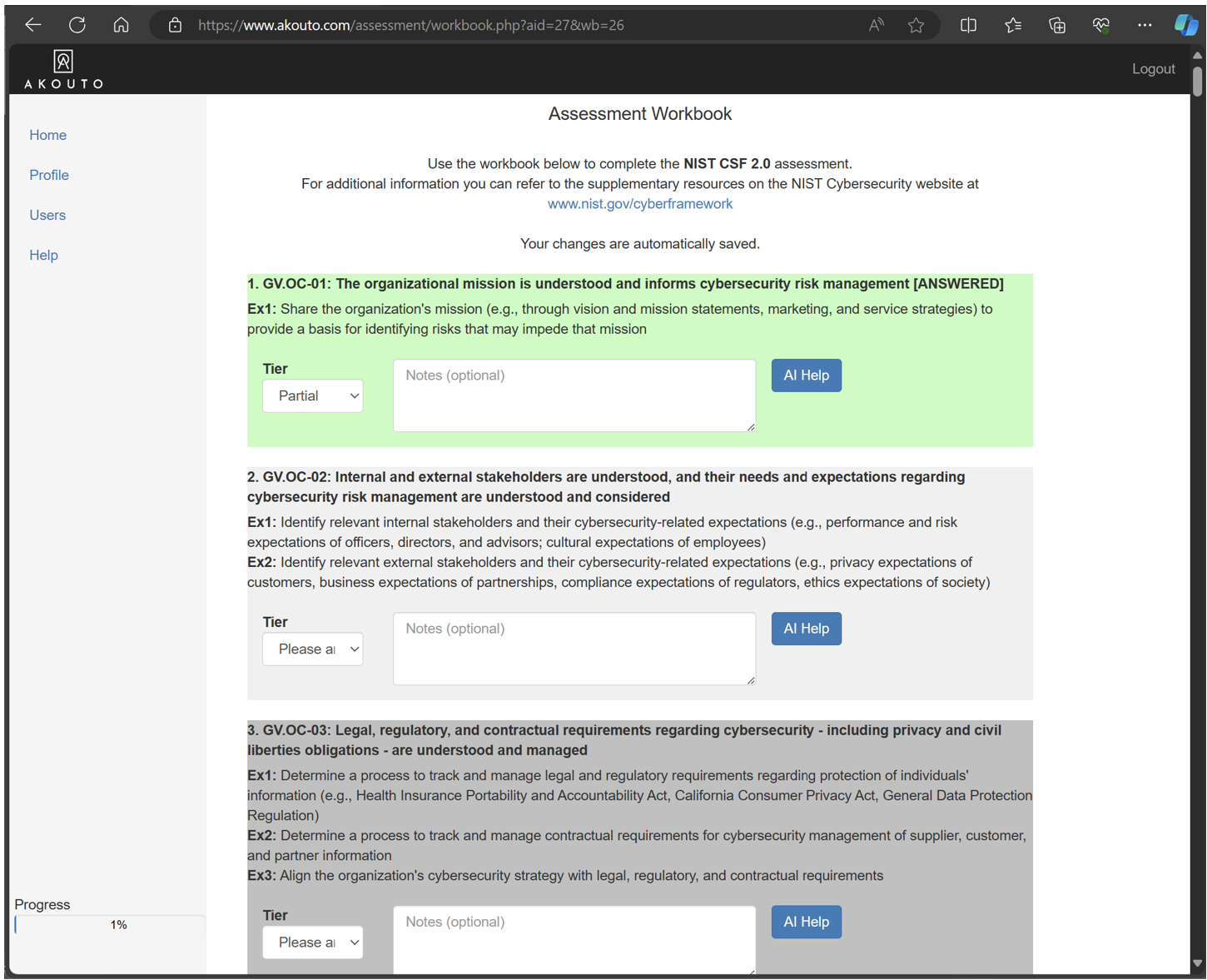
View progress
As you provide answers using the available form controls, questions that have already been answered will change to a green background. We will automatically save the form for you while you are working on it.
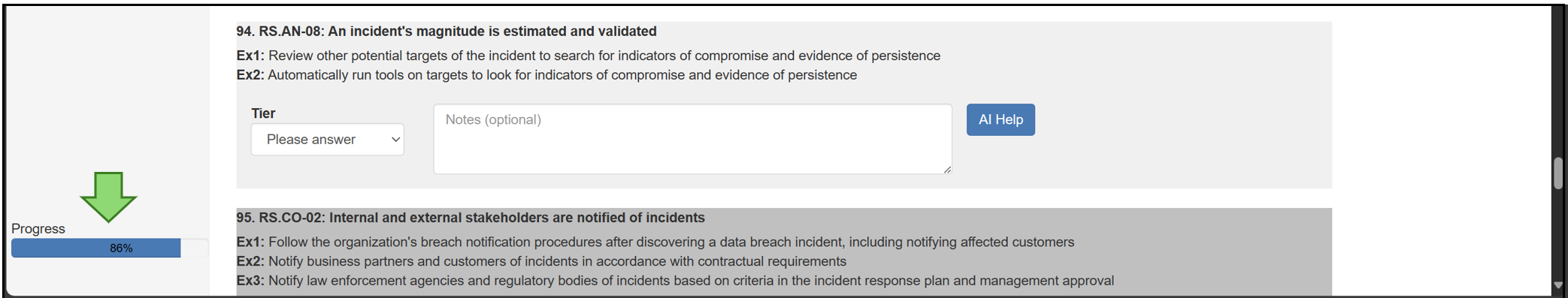
You can check your overall progress any time by checking the progress bar at the bottom left of the browser.
Top
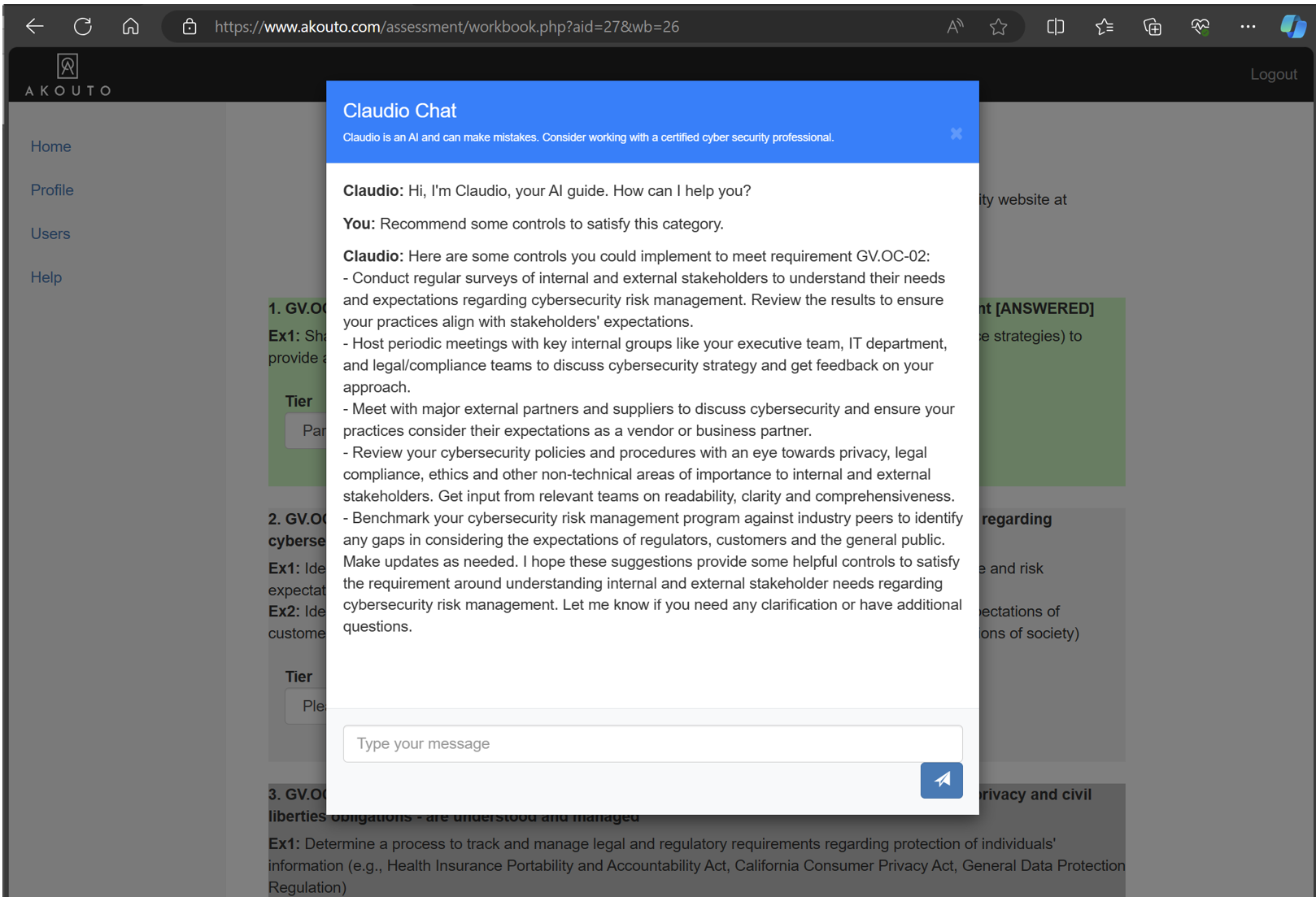
Use Claudio AI
If you need some help, just press the AI Help button and a chat box will allow you to chat with Claudio. Remember, Claudio is an AI and may make mistakes, it is always best to work with a certified cyber security expert.
Top
View a report
You can view the assessment report at any time to get a snapshot while you are working on it, or a final report once you are done.
You can see assessments that are in progress from the main landing page of the portal.
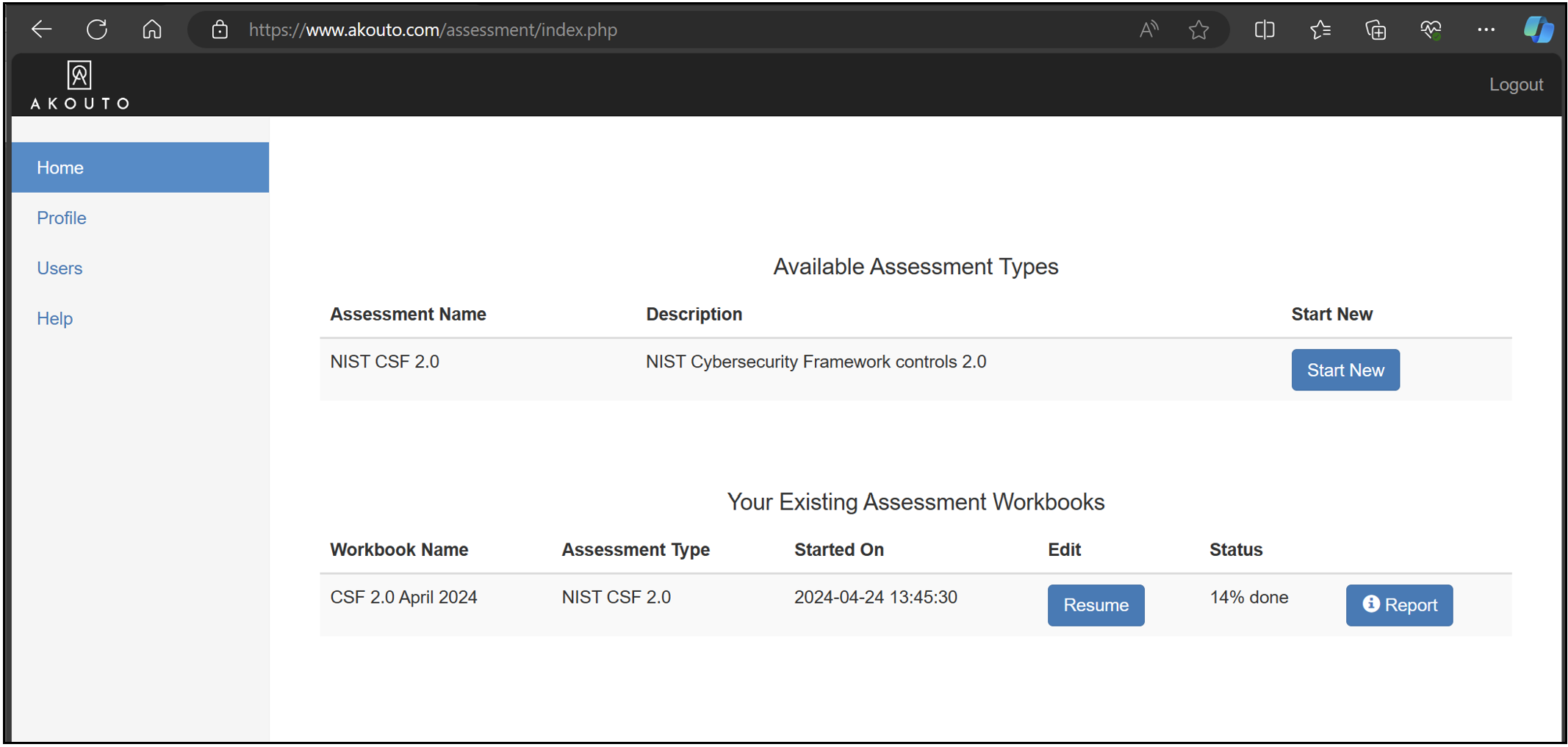
Press the Report button to get useful statistics and recommendations.
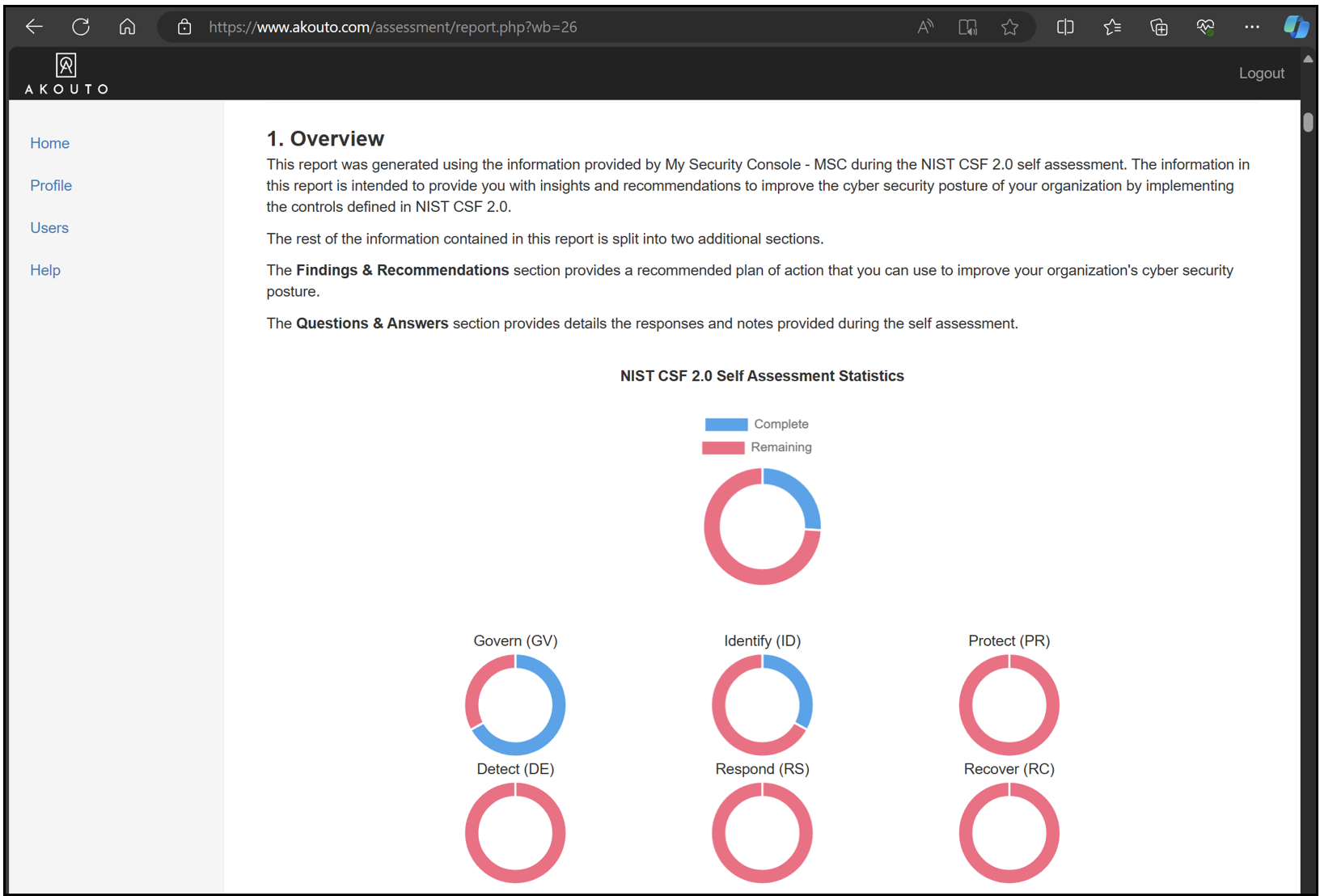
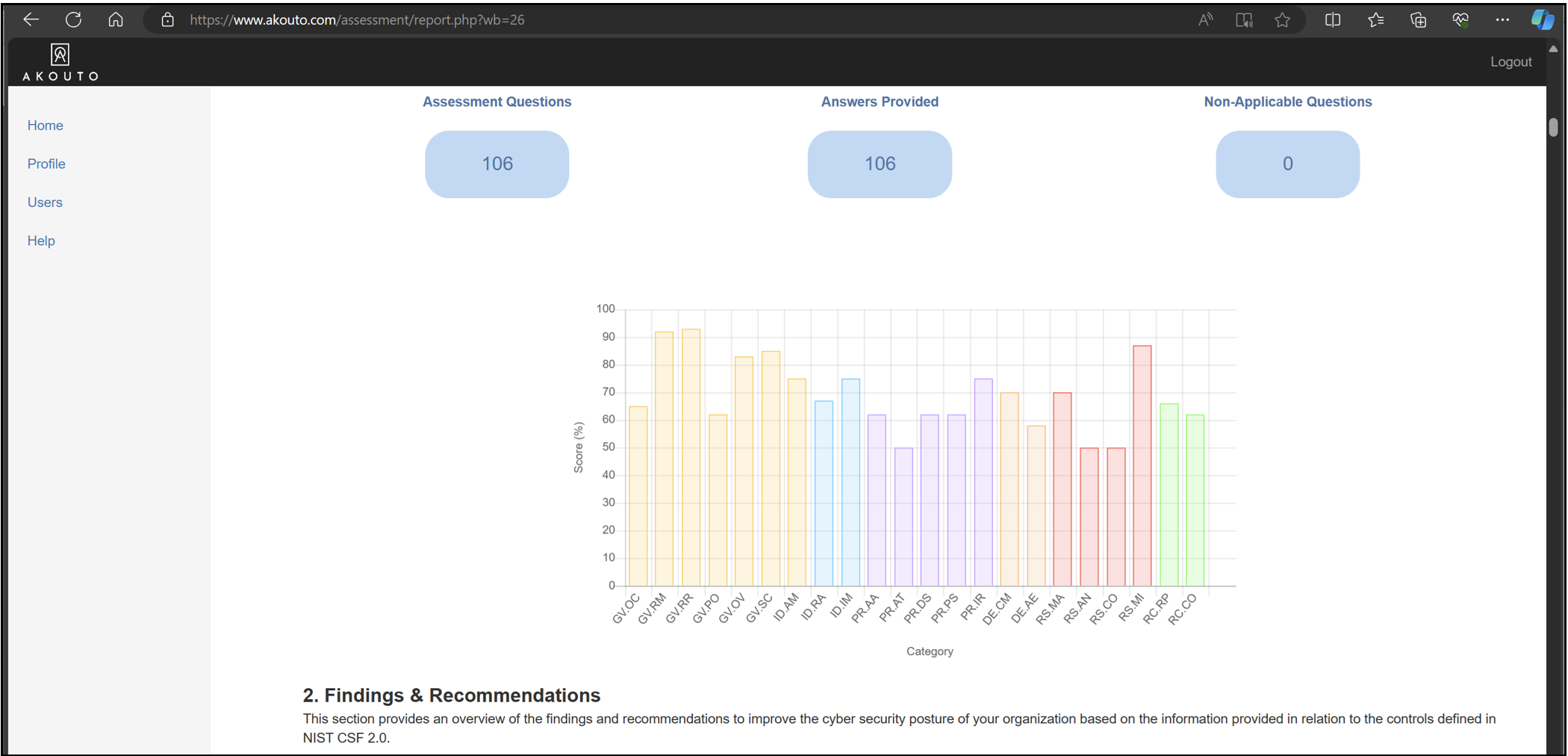
Top
NIST CSF Tier Selection
You can use the following description of the Tiers from Appendix B of NIST CSF 2.0 to help you choose what best describes your organization.| Tier | Cybersecurity Risk Governance | Cybersecurity Risk Management |
|---|---|---|
|
Tier 1: Partial |
Application of the organizational cybersecurity risk strategy is managed in an ad hoc manner. Prioritization is ad hoc and not formally based on objectives or threat environment. |
There is limited awareness of cybersecurity risks at the organizational level. The organization implements cybersecurity risk management on an irregular, case-by-case basis. The organization may not have processes that enable cybersecurity information to be shared within the organization. The organization is generally unaware of the cybersecurity risks associated with its suppliers and the products and services it acquires and uses. |
|
Tier 2: Risk Informed |
Risk management practices are approved by management but may not be established as organization-wide policy. The prioritization of cybersecurity activities and protection needs is directly informed by organizational risk objectives, the threat environment, or business/mission requirements. |
There is an awareness of cybersecurity risks at the organizational level, but an organization-wide approach to managing cybersecurity risks has not been established. Consideration of cybersecurity in organizational objectives and programs may occur at some but not all levels of the organization. Cyber risk assessment of organizational and external assets occurs but is not typically repeatable or reoccurring. Cybersecurity information is shared within the organization on an informal basis. The organization is aware of the cybersecurity risks associated with its suppliers and the products and services it acquires and uses, but it does not act consistently or formally in response to those risks. |
|
Tier 3: Repeatable |
The organization’s risk management practices are formally approved and expressed as policy. Risk-informed policies, processes, and procedures are defined, implemented as intended, and reviewed. Organizational cybersecurity practices are regularly updated based on the application of risk management processes to changes in business/mission requirements, threats, and technological landscape. |
There is an organization-wide approach to managing cybersecurity risks. Cybersecurity information is routinely shared throughout the organization./
Consistent methods are in place to respond effectively to changes in risk. Personnel possess the knowledge and skills to perform their appointed roles and responsibilities. The organization consistently and accurately monitors the cybersecurity risks of assets. Senior cybersecurity and non-cybersecurity executives communicate regularly regarding cybersecurity risks. Executives ensure that cybersecurity is considered through all lines of operation in the organization. The organization risk strategy is informed by the cybersecurity risks associated with its suppliers and the products and services it acquires and uses. Personnel formally act upon those risks through mechanisms such as written agreements to communicate baseline requirements, governance structures (e.g., risk councils), and policy implementation and monitoring. These actions are implemented consistently and as intended and are continuously monitored and reviewed. |
|
Tier 4: Adaptive |
There is an organization-wide approach to managing cybersecurity risks that uses risk-informed policies, processes, and procedures to address potential cybersecurity events. The relationship between cybersecurity risks and organizational objectives is clearly understood and considered when making decisions. Executives monitor cybersecurity risks in the same context as financial and other organizational risks. The organizational budget is based on an understanding of the current and predicted risk environment and risk tolerance. Business units implement executive vision and analyze system-level risks in the context of the organizational risk tolerances. Cybersecurity risk management is part of the organizational culture. It evolves from an awareness of previous activities and continuous awareness of activities on organizational systems and networks. The organization can quickly and efficiently account for changes to business/mission objectives in how risk is approached and communicated. |
The organization adapts its cybersecurity practices based on previous and current cybersecurity activities, including lessons learned and predictive indicators. Through a process of continuous improvement that incorporates advanced cybersecurity technologies and practices, the organization actively adapts to a changing technological landscape and responds in a timely and effective manner to evolving, sophisticated threats. The organization uses real-time or near real-time information to understand and consistently act upon the cybersecurity risks associated with its suppliers and the products and services it acquires and uses. Cybersecurity information is constantly shared throughout the organization and with authorized third parties. |