Recent Posts
- Integrating AI with conventional software
- From Ethical Duty to Legal Imperative: The Crucial Role of Secure Development in Today’s Software Industry
- Gone Phishing: Personalizing mass phishing with AI
- Elements of a secure development life-cycle
- Six Successful Strategies For Re-Opening Your Business After Covid19
- Cybersecurity Readiness in a Pandemic Era
- Cybersecurity In 2020 – A Roadmap To Keeping Your Business Safe
- What’s your reputation worth? The cost of not protecting your data.
- Ryuk Ransomware Hits Canadian Businesses
- Why Are Small Businesses A Hackers Playground?
- Phishing attacks targeting Office 365 users
- The new normal in cybersecurity
- Hackers targeting torrent sites
- The implications of PIPEDA for small business
- Cybersecurity Essentials
Integrating AI with conventional software
In this post I’ll be exploring some of the challenges with embedding generative AI capabilities within a conventional software application. By conventional I mean traditional applications that rely on structured programing, deterministic rules, and operate on pre-defined algorithms without incorporating AI techniques. First, a bit of background.
About NIST CSF 2.0
The NIST Computer Security Resource Center (CSRC) has long maintained one of the most respected frameworks used by cybersecurity professionals to “understand, assess, prioritize, and communicate cybersecurity risks”, the NIST Cybersecurity Framework (CSF). On February 26, 2024 they announced the availability of NIST CSF 2.0 along with supplementary resources that are all available for free from the CSRC website (https://csrc.nist.gov/news/2024/the-nist-csf-20-is-here).
This includes version 2.0 of the framework, quick start guides, resources specific to small businesses, implementation examples and more. The framework is organized around six risk management functions: Govern, Identify, Protect, Detect, Respond, and Recover. It can be tailored to help organizations of any size create and communicate a detailed view for effectively managing cybersecurity risk. It is an indispensable tool that can be used by small businesses, large enterprise, government agencies, schools; any organization regardless of size can tailor the framework to develop robust cybersecurity and risk management strategies.
Building a self assessment tool
To make the framework more accessible to smaller organizations without in-house cybersecurity expertise, we built a self-assessment web application with an integrated AI agent we called Claudio as a nod to Anthropic’s Claude family of Large Language Models. Claudio can answer questions related to NIST CSF 2.0, provide guidance needed to complete a self-assessment and generate recommendations based on a risk profile established by asking the user a few simple questions. The tool is available for free online at https://www.akouto.com/assessment/
Anthropic Claude vs OpenAI ChatGPT
During the research stage, two competing implementations were developed: one using the OpenAI Assistant API, and the other using Anthropic’s Claude AI on AWS Bedrock. Claude quickly became the clear winner with a more intuitive API and better response times. Claude was also better at interpreting and following prompts. Even with Claude’s advantages there were still some interesting discoveries while trying to integrate generative AI with traditional software.
Application Design
Users interact with Claudio through an HTML form. Every interaction is an HTTP POST where the user submits their question (or answers to Claudio’s questions) using a basic HTML form. The web application is written in PHP, and the form data is handled by a Form Processor which performs the security checks and input validation.
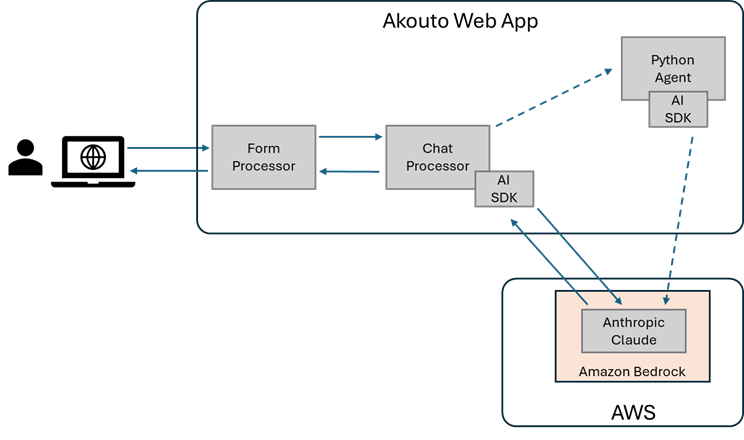
Rather than have the Form Processor directly interact with the AI API, an intermediate Chat Processor was implemented. This is where Claudio lives, it’s where the AI prompts are created to interact with AWS Bedrock and the LLM using the SDK provided by Amazon.
Another approach using a Python daemon was implemented to evaluate possible benefits of using the Python SDK instead, but since no real advantages were identified, the Python Agent approach was set aside.
Chat Processor
One of the responsibilities of the Chat Processor is to generate the prompts that are used when interacting with the LLM. The prompt is created by combining the information submitted by the user with additional inputs following a well-defined structure:
Task context: In this section we define the role and persona of Claudio the AI Cybersecurity advisor.
Tone context: In this section we instruct the LLM on the tone it will use when interacting with users.
Background data: In this section we provide information that is relevant to NIST CSF 2.0.
Rules: In this section we define the rules of engagement. We define the do’s and don’ts of Claudio’s interaction with users.
Examples: In this section we provide the LLM with concrete examples of what different interactions might look like.
Data: In this section we provide the conversation history and the user’s question (or answer)
Instructions: In this section we provide additional instructions to apply specific prompting techniques
Output formatting: In this section we provide instructions on the format of the expected response
The old and the new
One of the interesting aspects of the design approach was the ability to combine traditional software development with AI interaction to improve the overall solution including response times, accuracy rate, better understanding of context and more precise execution of tasks.
Instead of using hard-coded prompts and just appending the user input, different sections of the prompt are generated programmatically based on context. The context includes what the user is working on, past interactions, and information previously returned by Claudio among others. Tailoring the prompt for each interaction in the chat session yielded much better accuracy throughout the conversation.
To minimize opportunities for misuse, guardrails are built into rules section of the prompt. One approach would be to first submit a verification prompt to the LLM asking if any of the rules are violated before proceeding with the interaction. This approach uses significantly more tokens (and therefore costs more) and also doubles the interaction time which has a significant impact on user experience. One of the solutions was to include instructions in the input prompt for Claudio to include two distinct sections in the response: a reply to the user’s input, and a rating of the appropriateness and relevance of the input. By providing detailed instructions on the format of the response and rating sections, the Chat Processor is able to programmatically detect and mitigate misuse attempts.
XML tags proved to be extremely valuable for formatting both prompts and responses. This might be more successful with Anthropic’s Claude than other LLMs, but accuracy significantly improved by clearly identifying different sections of the input prompt using XML tags, and instructing the LLM that different sections of the response should also be delimited with XML tags to allow for post-processing by the Chat Processor. This post-processing step allows the Chat Processor to decide whether to pass through the AI response, or take some other actions depending on information contained within specific XML tags.
Risks
There’s an aspect to integrating AI with traditional software that is difficult to come to terms with from an Engineering perspective. Up to now there has not typically been room for ambiguity in software engineering. Requirements, features and functions must be well understood and are expected to work correctly 100% of the time in a completely predicable way. If they don’t, that’s a bug that needs to be fixed. With the current state of AI, this mindset just isn’t possible. Regardless of how much prompt engineering and fine tuning you do, models sometimes perform in unpredictable ways, and can even generate incorrect results. For some use cases, that’s ok as long as we’re all aware of the fact that we need to use critical thinking, verify information produced by generative AI, and be open to occasional surprises.
From Ethical Duty to Legal Imperative: The Crucial Role of Secure Development in Today’s Software Industry
I love my job. As a Computer Engineer in the tech industry, I consider myself very lucky to work with talented and innovative people bringing new ideas to life and solving real-world problems. Every day I’m excited to dive into new technical challenges to help build and secure the digital infrastructure that powers our world. However, there is also a pressing concern with the industry that we cannot afford to ignore. In a world of startups, IPOs, and tech billionaires, the industry has become increasingly hyper-focused on monetary gains, too often sidelining safety and security in the relentless pursuit of market share and profit. Not that those are bad things, there would be no tech industry without them, but in the absence of proper checks and balances, this alarming trend not only endangers our digital ecosystem but also compromises the values that should guide our collective progress.
As an industry, we can do better and we need to take action. It’s no longer just a question of ethics either, political leaders are now paying attention to this issue and policymakers are taking steps to hold the tech industry accountable. The recently announced National Cybersecurity Strategy in the US explicitly mentions a plan to shift liability for software products and services to promote secure development practices. The days of software license agreements that allow tech companies to absolve themselves of any and all responsibility for the shortcomings of their products are coming to an end. It has already begun in the medical industry with a new law that requires medical device manufacturers to submit evidence to the FDA that devices can be updated and patched, provide information about security controls and testing, and list the commercial and open-source components that are included in the product.
The integration of security in all aspects of software development has moved from being a best practice to being a strategic enterprise requirement. Establishing a secure development lifecycle does not happen overnight, it requires a cultural shift and organizational changes along with the appropriate mix of tools, policies, and procedures. To remain competitive in an environment of daily cyberattacks and increasing regulatory oversight, tech leaders need to motivate and empower their teams to integrate security measures throughout the development process and emphasize the need to develop secure and robust solutions.
Software security can be significantly improved by leveraging established frameworks, like DevSecOps, Microsoft SDL, and ISO 27034 among others, to implement a secure development lifecycle. By adopting DevSecOps principles, organizations can foster a culture of collaboration and shared responsibility for security among development, operations, and security teams. Microsoft SDL offers a proven methodology for integrating security and privacy requirements at every stage of software development, from planning to deployment. Similarly, ISO 27034 provides a systematic approach to application security, focusing on risk assessment, management, and mitigation. By leveraging frameworks like these and tailoring them to their specific needs, organizations can create a robust, secure development lifecycle that addresses potential vulnerabilities early on and promotes a proactive security mindset across the entire product development process.
The tech industry needs to strike a balance between innovation and security to ensure continued growth and success. As the landscape evolves, it is essential for organizations to prioritize secure development practices and foster a culture that values safety alongside profitability. By leveraging established frameworks, companies can create a tailored secure development lifecycle that effectively mitigates vulnerabilities to protect systems and data against cyberattacks while safeguarding the trust of users and regulators alike.
If your organization is looking for some ideas on how to get started, check out my previous post on the Elements of a Secure Development Lifecycle, these Microsoft SDL resources, the OWASP Application Security Verification Standard, or feel free to reach out if you have any questions.
Gone Phishing: Personalizing mass phishing with AI
I’ve used AI libraries and APIs on a few different projects, using it for things like anomaly detection in large IoT datasets and for advanced threat detection capabilities in My Security Console. I feel compelled to also credit AI for the image that is part of this blog post, it was created in a matter of minutes by OpenAI’s DALL-E model simply asking for “A realistic image of a humanoid robot on a boat fishing”. But I digress; with all the stories in the news about AI and ChatGPT, I was recently asked to share some thoughts about how AI is being used by the “bad guys” to perpetrate scams or carry out cyberattacks.
Hackers are a creative bunch and there’s no telling what innovative (albeit nefarious) uses of AI will surface as tools like ChatGPT become more mainstream and capable. Blogs posts from Check Point Research show how these tools can be used to create a full infection flow, and that AI-generated code is already starting to appear in Dark Web hacker forums.
There are also documented cases of AI being used in social engineering attacks, like the case of AI voice cloning being used to authorize $35M in fraudulent bank transfers, and in fake kidnapping scams where a person’s voice is cloned using speech samples from videos posted to social media accounts and then used to convince loved ones to pay a ransom for their safe return.
While these types of attacks can be devastating, they are relatively small-scale because they are highly targeted requiring time and skill to set up, and carry a much higher risk for the perpetrators to be brought to justice. In comparison, simpler phishing attacks that attempt to steal login credentials or credit card information are much easier to carry out by email and can be launched against hundreds of thousands of potential victims with minimal risk to the perpetrators. The average click rate of a mass phishing campaign is somewhat low, mostly because so many of the emails are generic and unconvincing. Having said that, phishing is the second leading cause of data breaches and the costliest attack vector due to the impact and time to identify & contain. This is an area I expect we will see AI used successfully in large-scale phishing attacks in the very near future, with research already showing that AI-generated phishing email is nearly two times more successful at getting victims to click on a link or open an attachment.
With that in mind, I set out to see how difficult it would be to write code that could carry out an AI-assisted mass phishing campaign with a twist: one that sent well-written personalized messages to the victims. After some initial research, I decided to code it in Python and use the API for OpenAI’s text-davinci-003 model. Since I had been asked to provide a demonstration of how this could work, I created a simple program that scrapes a potential victim’s online bio and sends a fake recruiting email with malicious links and attachments. It turns out this is really easy to do in no time with just a couple hundred lines of code. Each API call to text-davinci-003 that took a scaped bio and generated a customized phishing email took about 10 seconds on average to complete with a single thread, so doing this at scale would require a multithreaded approach, but that can be quickly coded with very little effort.
Based on my experiments, at current price levels it would cost approximately $800 to generate 100,000 personalized mass phishing emails. On average, stolen account credentials sell for around $15 per account on the Dark Web, even with a modest success rate of 2% in the generic phishing scenario, the haul from a phishing campaign with 100K targets jumps from $30,000 in the generic case to $60,000 when using AI-generated custom messages, well worth the $800 cost. You might hope that companies will take steps to prevent AI from such misuse, but looking at how much the online advertising industry does to stop malvertising I’m not overly optimistic that profit won’t come first in this case too.
With far more effective phishing campaigns on the horizon, it is important to focus on prevention to avoid falling for these scams, so here are a few tips to keep your business safe:
- Don’t select an email provider purely on price, use a reputable vendor with strong anti-malware and phishing protection.
- Use multi-factor authentication for access to accounts and data.
- Monitor for suspicious activity on company networks using a Managed Detection and Response service like My Security Console.
- Educate employees on phishing scams and how to spot them, provide regular training and reminders to employees about the importance of security.
- Institute security policies that require employees to use strong passwords, MFA, and regularly take cyber awareness training.
- Use a multi-layered approach to security that includes email filtering, intrusion prevention, and anti-phishing tools.
Elements of a secure development life-cycle
I’ve been coding ever since I got my hands on a TRS-80 with its impressive 16K of RAM and 8-bit microprocessor in the mid ‘80s. Anyone up for a game of Cuthbert Goes Walkabout?
A lot has changed since then, but the things I love most about coding are still the same: solving tricky problems and getting to see your ideas come to life. One of my personal challenges is reining in my enthusiasm to see the end result, taking a deep breath, and making sure to do all the things along the way that make the difference between writing good code and writing awesome code.
That is especially important to do when thinking about cybersecurity. Granted, some of those things can be time consuming, and the truth is that they do add time and cost to development projects. But what is the cost of cutting corners? Sure, you may save a few dollars by skipping some steps, but with minimum ransomware demands being in the tens of thousands now, that’s hardly a bargain.
On a positive note, development teams are becoming aware of the need to weave cybersecurity into the development life-cycle, but it isn’t always clear what that entails, so here is a list of things for your organization to consider. This is by no means an exhaustive list, and if it seems like a lot to take on, remember that it doesn’t have to be all or nothing, starting with the basics and having a continuous improvement plan is a great way to begin.
People
- Training: People are often the weak link when it comes to cybersecurity. Annual cyber awareness training has proven to be quite effective at reducing cybersecurity incidents, along with role-specific training to make sure your development team is up to date with the latest threats and best practices.
- Leadership: Your cybersecurity program can only succeed if there is commitment across the organization and this starts at the top. Leaders need to be clear on their expectations and organizational objectives when it comes to cybersecurity.
- Accountability: Objectives and expectations are meaningless without accountability. People must be aware of expectations and be held accountable for their actions (or inaction).
- Response team: A security response team & process should be established that can quickly respond to threats or incidents when they do arise.
Process
- Security requirements: When defining product requirements it is important to take the time to identify security requirements to make sure the solution and the information it processes are adequately protected.
- Threat modelling: Applying a methodical process to identify potential threats and vulnerabilities is a necessary first step in ensuring there are adequate safeguards built into the solution.
- Security design reviews: Designs need to be assessed from a security perspective to verify that the threats and risks have been appropriately factored in at the architecture & design level.
- Secure coding: A secure coding policy or guidelines should be established and enforced to ensure that developers apply best practices during the implementation phase.
- Code inspections: This practice has been around for a long time and is proven to reduce the number and severity of software defects. Developers should be trained on security best practices and ensure those are followed throughout the inspection process.
- Security Testing: Test plans should have a category explicitly dedicated to security testing to ensure the application meets the defined security requirements and is free (to the extent possible) of defects that introduce security vulnerabilities.
- External Dependencies: It should not be assumed that external components integrated into the application are secure. Third party software should be explicitly tracked on every release including knowing what version is in use and what known vulnerabilities are present by checking vulnerability databases.
- Penetration testing: The last chance to identify vulnerabilities before releasing an application or software update is to engage a seasoned penetration tester to identify weaknesses that hackers will try to exploit.
- Change management: There should be an established and enforced change management process to control what code is checked in, by whom and for what reason.
- Patching: Despite best efforts, defects will happen and vulnerabilities will be discovered. There needs to be an established security patching and upgrade process to make sure vulnerabilities can be addressed in an efficient and timely manner.
- Gates: The development process should include specific gates that are checked before the software is allowed to proceed from one stage to the next. For example, before and application or update can be released, development leaders should verify that there was a security design review, code inspections took place, security testing was performed and so on.
- Automation: In order to minimize human error in the development process, a secure, repeatable & automated build/test/deployment process and infrastructure should be established and utilized.
- Budget: When establishing a budget for the development organization or a particular project, there should be time and money allocated specifically for security in order to give the development team the necessary tools and resources.
- Measurements: The performance of the secure development process needs to be measurable. This is done by establishing and tracking secure development process Key Performance Indicators such as compliance status per release, percentage of security test cases, number of major and critical vulnerabilities found during testing per release, number of security defects found during testing, number of security defects found in production to name a few. The information should be periodically analyzed and used to improve the process.
- Audits: The security program and processed should be periodically audited to make sure expectations are understood, established policies and procedures are being properly applied and objectives are being met. This is not intended to be punitive, but rather to identify weaknesses in the secure development process and plan improvements.
- Policies: Secure development policies need to be detailed and specific covering everything from the procedural elements of the secure development process all the way down to specific technical details such as approved tools, required compiler flags, acceptable crypto suites, etc.
Technology
- Access control: Access to the software repository must be restricted to authenticated and authorized users only following the principle of least privilege to reduce the risk of accidental or malicious introduction of vulnerabilities into the source tree.
- Repo scanning: The source code repository should be automatically scanned on a regular basis to identify vulnerabilities that may be present in third-party or in-house components.
- Static code analysis: Static code analysis tools should be used to automatically check the code for issues such as buffer overflows, the use of insecure functions and libraries, etc.
- Vulnerability scanning: Automated vulnerability scanning tools should be periodically used to identify any vulnerabilities that may have been discovered since the last scan. This can help quickly identify and mitigate vulnerabilities that are discovered over time.
- Integrity protection: Mechanisms such as code signing should be used to verify the integrity of software releases, patches, upgrades or any component integrated with the application.
- Compiler: Secure compiler settings should be identified, documented and enforced to prevent insecure code from introducing vulnerabilities.
- Hardening: Endpoint hardening should be applied to all endpoints including developer systems, servers and infrastructure in both the development and production environments.
- Monitoring: Security specific monitoring and alerting should be built into the application that can help identify anomalies that indicate an attack or breach once the system has been deployed.
If all of this seems daunting don’t be discouraged. It doesn’t all have to be done overnight and there are lots of free resources that can help. One of my favourites is the OWASP Cheat Sheet Series which provides an extensive list of well written cheat sheets covering many application security topics. Pick a few of the items from the list above that you think you will be able to implement in the next few months, and check out the cheat sheet series for resources that might help.
Six Successful Strategies For Re-Opening Your Business After Covid19
By Dom Chorafakis, P.Eng, CISSP – May 27, 2020
Reopening your business successfully requires more than a return to normal. The sudden widespread closures found many businesses scrambling to adapt and sadly some of them have not survived.

Organizations with Business Continuity Plans found themselves a step ahead of those who had little to no planning, and now as Canadians grapple with managing life during the covid19 pandemic, some things are coming to light about what we can do as individuals and as business to resume working and living within the new restrictions.
Resources like those from the Ontario Government provide details around workplace and worker safety, and although many practices are consistent among all provinces, business should explore their specific provincial website for what is required in each province.
So how do you begin?
- Put People First: Returning employees will have some fears and questions about their safety in the workplace. Ensure that your organization has clearly defined workplace safety procedures and protocol and communicate those procedures clearly and often with your staff. Creating a safe work environment for staff and clients is key to a successful re-opening.
- Check Health & Safety Equipment: Perform maintenance on health and safety equipment (e.g. smoke detectors, fire alarms, security and PA systems) that may have been missed during the shutdown and confirm they are working as expected.
- Complete Software Updates: Computers that have been powered off for some time have not been receiving Windows updates. You should:
- Make sure you back up important data before applying updates as they sometimes may cause problems
- Manually go through the update process to ensure the PC is fully up- to-date before using it to access email or the Internet
- Perform Laptop Checks: Computers that were being used at home in a less controlled environment may be infected and spread malware on the corporate network.
- Make sure all systems in the office are up-to-date with software and anti-virus updates
- Perform a full scan of any systems that were used outside of the office during the shutdown
- Inspect Battery Backups: UPS and backup batteries may not have been checked or maintained during office closures. Inspect battery backups to verify that charge levels and expected duration in the event of a power outage are in accordance with battery capacity and load.
- Re-Train Staff: Your employees are your best resource for identifying and resolving issues. Some things may have fallen through the cracks so be sure that staff are refreshed on critical business protocol, which should include cyber safety. 60% of all security breaches come from internal staff, so reminding your staff about cyber safe practices like password management and email threats is critical to the safe re-opening of your company.
Re-opening your business will take special care and planning, especially as it relates to cyber security requirements so we’ve created a list of free resources to help you build your plan. To receive the list and to learn more click here.
Cybersecurity Readiness in a Pandemic Era

By Dom Chorafakis, P.Eng, CISSP - March 2, 2020
As the coronavirus (COVID-19) continues to spread around the globe, and with the first suspected instance of community spread in the U.S confirmed by the CDC, time is quickly running out for individuals and businesses to prepare for the inevitable disruptions of an outbreak. Business Continuity and Disaster Recovery planning are two critical components of a good cybersecurity strategy. These plans ensure that a business has the necessary systems and procedures in place to enable ongoing operations during a crisis, and allow them to quickly and efficiently resume normal operations once the crisis is over.
There is no doubt that a coronavirus outbreak will have a significant economic impact on businesses, especially those located in affected areas. The 2003 SARS outbreak in Toronto which saw 375 cases in the 110 days between February 23rd and June 12th 2003 is estimated to have cost Toronto businesses approximately $1 billion. With the worldwide number of COVID-19 cases already 10 times higher than the total number of SARS cases in 2003 and no end currently in sight, the economic impact is expected to be much more severe.
Many large corporations have Business Continuity and Disaster Recovery plans in place and regularly test those plans to make sure they are ready to respond when disaster strikes. Unfortunately, most small and medium businesses lack the expertise and resources and are unable to cope with a crisis. To help businesses prepare for the anticipated disruptions caused by a COVID-19 outbreak, organizations such as the U.S Centers for Disease Control (CDC) have provided guidance that businesses of all sizes can use to develop strategies specifically for a coronavirus outbreak and emergency planning in general.
Being proactive and having a plan in place is critical to a business’s ability to survive a crisis. There are lots of great resources out there that people can use to help them build robust Business Continuity and Disaster Recovery plans, although details can be a bit sketchy when it comes to cybersecurity. It’s also important to remember that this isn’t something that’s done once and put on a shelf, it needs to be an ongoing practice.
Ongoing cyber-awareness training is one such example. Cyber criminals often take advantage of major global events as a way to trick users and infect systems, the threat of a COVID-19 pandemic is no exception. Security researchers have already reported several scams involving email that claims to be from HR with updates on company staff affected by the virus or updates from the WHO or CDC with attachments that are used to install ransomware and other malware. In light of the fear and confusion surrounding the coronavirus outbreak, employees should be reminded to be vigilant and suspicious of email claiming to provide information or updates about the virus.
Businesses need to make sure their continuity plans cover a wide range of topics like ensuring employees have secure remote access to critical business systems, having a secure way for people to share files if they need to work remotely for extended periods of time, or being able to communicate with customers in the event a facility is quarantined. This can all be a bit daunting, so we’ve created list of free resources businesses can use to help them build their plan which is available here.
Cybersecurity In 2020 – A Roadmap To Keeping Your Business Safe

By Dominic Chorafakis, P.Eng, CISSP – January 31, 2020
A look back at 2019 tells us all we need to know about what we can expect in the world of cyber threats for 2020. The past year saw the return of the Ryuk virus hit the Canadian market targeting three Ontario hospitals and a Toronto dental clinic in which the attacker encrypted the clinic’s files and demanded $165,000 in ransom in order to restore access to the files.
The recent LifeLabs data breach is the largest yet in Canada in terms of personal record count, and the company may end up paying dearly for its security lapse. A civil lawsuit that was just introduced in Toronto is seeking a total of $1.14 billion dollars in damages. 
We know that incidents of cybercrime are on the rise, and a StatsCan report found that one-fifth of Canadian businesses reported that they were impacted by a cyber security incident.
Cyber threats have become main stream and now regularly make the news. Statistics show us that companies large and small are not exempt from the threats of cyber criminals looking to access their company info and steal their data. In fact security sources predict that nearly half of the cyber-attacks for 2020 will be on small businesses.
So How Can We Use The Events From Last Year To Prepare For The Year Ahead?
The first step is to accept that cyber threats are here to stay. In today’s world all businesses small and large are connected to the web and a network of external sources and potential openings for threats to pass through. Many of these threats simply didn’t exist in past years but they are here now and they aren’t going anywhere. Business that choose to adopt an “it won’t happen to me” approach are at the greatest risk, and with the average cost of a hack for small and medium Canadian business being in the range of $46,000 to $100,00 dollars it’s a risk many business will find too hard to recover from. But it’s not too late. Here are three simple suggestions to get you started.
- Have a plan – Work with your IT support staff to create a plan that details the steps you should take to prevent an attack along with the steps to take in the event of an attack. This will not only reduce your risk, it will also reduce the impact of an attack so your business can be up and running in no time.
- Train your staff – Statistics show that 60% of all security breaches come from internal staff, so creating cyber awareness internally is a key safeguard for your company.
- Apply a multi-layer approach to security – make sure that you install anti-virus, anti-spyware and intrusion prevention tools and that you routinely update the software and operating programs that you use to run your business. Adopting a security monitoring solution is the final layer in a comprehensive package.
Staying ahead of the threats is an everyday challenge and not one that most business owners can, or should manage alone. The good news is that tools to fight cyber threats have also been growing and now more than ever business have the resources available to help them protect their data.
What’s your reputation worth? The cost of not protecting your data.
By Dominic Chorafakis, P.Eng, CISSP – November 12, 2019

Businesses spend a lot of money building and maintaining their reputation. Recent information from the Business Development Bank of Canada (BDC) indicates that Canadian small business marketing costs average just over $30,000 a year, while those with 20 to 49 employees spend twice that amount. Companies with 50 or more employees tend to have marketing budgets in excess of $100,000. Unfortunately, many businesses fail to protect this investment and make the costly mistake of damaging their reputation by not protecting their business and client data.
Clients view their information as extremely valuable and expect companies that have it to protect it. They not only expect it, but also have legal rights that allow them to push back on organizations that don’t follow the rules. As of November 1 2018, the government of Canada has made changes to its Personal Information Protection and Electronic Documents Act (PIPEDA) requiring all organizations that hold personal information to report any significant data breaches.
The value of your reputation
The immediate business costs and disruptions caused by a data breach can be painful, but what is often more impactful and long lasting is the loss of customer trust and erosion of the company reputation. According to the IBM Ponemon Institute, 36% of the cost of a data breach comes from the loss of business stemming from loss of customer trust after a cyber incident. The message is clear, if you don’t value a customer’s information enough to protect it then you don’t value their business. A recent Verizon survey on Customer Experience found that 29% of customers would never do business with a company again if they were personally affected by a data breach.
Think about the impact that data breaches have had on a larger corporation like Marriott Hotel which lowered the company’s revenue by three million dollars following its 2018 data breach announcement. While large corporations have extensive resources and deep pockets that allow them to ride out the storm and slowly build back their reputation, small-to-mid sized businesses (SMBs) are not often not equipped with the knowledge, resources, or budget to build back customer trust which can result in an unrecoverable loss to their reputation and revenue.
Reduce your company risk
To stop your company from experiencing these damages, it is essential that you have rigorous control over the personal and client data that you handle. Avoid the all too common mistake that SMBs make of thinking that they are too small for hackers to care about. At a recent Cybersecurity For Business Leaders event in Toronto, Robert Gordon, executive director of the Canadian Cyber Threat Exchange (CCTX) stated that “Attackers will often go after a small business as an entry point to a larger target.”
Educate yourself and your staff about the risks, prepare your business with the tools needed to protect your data and finally adopt a managed cyber security service that can help identify vulnerabilities and improve security to catch threats before they become an issue. Protecting your company and clients data from cyber threats is a business imperative, your company’s reputation and viability depends on it.
Ryuk Ransomware Hits Canadian Businesses
By Dominic Chorafakis, P.Eng, CISSP – October 22, 2019
The Ryuk ransomware virus is back and it’s targeting Canadian businesses and industries. The virus first appeared in the summer of 2018 and then again in January of this year, its victims largely in the UK and USA. Recently however hackers have set their sights on the Canadian markets hitting three Ontario hospitals and the most recent victim a Toronto dental clinic in which the attacker encrypted the clinic’s files and demanded $165,000 in ransom in order to restore access to the files.
Ryuk is not limited to targeting a specific industry and there is an increase in the number of Canadian businesses that are affected by such cyber attacks.

How Does It Work?
The initial Ryuk infection is most frequently caused by a spam email that contains a malicious attachment. Once the malware manages to install itself on a computer, it is able to bypass anti-virus detection and often remains hidden for months.
During that time, it collects information about the organization and uses Windows vulnerabilities and other tricks to spread to other computers. Once enough systems have been infected, a remote command is given which causes all files to be encrypted and a ransom note is posted. Ryuk then locks files, demanding the network owner pay a sum of money to make them accessible again.
What you need to know
Unlike other modern ransomware like Wannacry, Ryuk itself possesses functionality that goes beyond the ability to identify and encrypt network drives and includes the ability to delete shadow copies on the endpoint. By doing this, the attackers could disable the Windows System Restore option for users, and therefore make it impossible to recover from the attack without external backups.
For individual users or small businesses unaccustomed to backing up their data this time of information loss could be devastating.
Many unsuspecting victims assume that paying the ransom fee will resolve the situation unaware that there is no guarantee of getting back all, or any of the stolen data, often compounding the severity of the situation by adding a financial victimization to the data loss.
So how do you protect your data?
- Develop cyber smarts – Computer users should be aware of how to spot phishing email and receive cyber awareness training.
- Get the right tools – Although Ryuk can bypass anti-virus, it is possible to detect its activity on the network by monitored intrusion prevention systems like My Security Console. The right software combined with monitoring by cyber experts can prevent infection or cut it off before it spreads.
- Have a backup plan – You just learned how paying ransom doesn’t mean that you’re out of the woods, in many cases infected files are damaged and not recoverable. Safe backups are the only reliable way of recovering your data should you become infected – so be sure to routinely backup your data!
Want to learn more about how to stay cyber safe?
Discover how you and your team can develop the skills needed to avoid becoming victims of ransomware attacks like Ryuk – take our free phishing training here.
Why Are Small Businesses A Hackers Playground?
By Dominic Chorafakis, P.Eng, CISSP – September 11, 2019
 Today’s small and medium businesses are increasingly a favourite target for cyber criminals. The government of Canada‘s most recent cybersecurity threat report states that business of all sizes are vulnerable. Hackers and cyber criminals don’t discriminate based on company size, location, or annual revenue; they simply look for the easiest way in, which is through an unprotected system most often found in a small business. “Businesses can no longer rely on anti-virus alone to protect their systems and applications,” said Bruno Macchiusi, founder of Toronto-based IT Service Provider Alpha Logics. “We’re seeing a large number of attacks that are able to bypass anti-virus these days”.
Today’s small and medium businesses are increasingly a favourite target for cyber criminals. The government of Canada‘s most recent cybersecurity threat report states that business of all sizes are vulnerable. Hackers and cyber criminals don’t discriminate based on company size, location, or annual revenue; they simply look for the easiest way in, which is through an unprotected system most often found in a small business. “Businesses can no longer rely on anti-virus alone to protect their systems and applications,” said Bruno Macchiusi, founder of Toronto-based IT Service Provider Alpha Logics. “We’re seeing a large number of attacks that are able to bypass anti-virus these days”.
What are the top 3 biggest mistakes that small & medium businesses make?
- They think that they are too small to be of interest to hackers
- They lack knowledge of the simple steps that they can take to prevent becoming victims
- They assume that security solutions are too costly and only for large organizations
Recent updates to laws like Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA) makes organizations that hold personal staff, client, or member information accountable to report any significant data breaches; this includes breaches in small to medium businesses. The legislation means that companies can no longer hide if they’ve been victims of a cyber-attack. This type of disclosure can seriously damage a company’s reputation (remember Equifax?). Small and medium size businesses are often poorly informed and can be blinded-sided by their legal responsibilities making them more vulnerable to the fallout from an attack.
We know that incidents of cybercrime are on the rise, a recent StatsCan report found that one-fifth of Canadian businesses reported that they were impacted by a cyber security incident. Recovery costs are also on the rise and range from $113,000 for medium-sized businesses (50 to 249 employees) to $46,000 for small businesses (10 to 49 employees).
So how do businesses keep themselves protected from hackers?
Expect that you’ll become a victim and plan ahead. There are many security measures that can help keep you and your data safe, but nothing can guarantee you 100% protection. Being prepared can reduce the impact, cost and time of recovery. Here are our top 5 tips on how to be cyber safe.
- Back-Up Your Data – so if your company information has been stolen or is being held for ransom you can refer to your back-ups and be up and running again with minimal downtime.
- Install the right protection software – make sure that you install anti-virus, anti-spyware and internet firewall tools.
- Keep your operating system up-to-date – try to keep your systems updated with the newest version available. These updates have important security patches and fixes that will protect against the latest threats.
- Employ good email and internet habits – one the most popular tools that hackers will use to attack you is through phishing emails and visiting infected sites (malvertising). Clicking on suspicious links or downloading malicious files are common ways that you and your staff can let hackers into your business.
- Consider a monitored security solution – many businesses make the fatal mistake of thinking that these types of solutions are too costly or complex for them. Services like My Security Console allow businesses to enjoy enterprise-grade security features for small business prices.
Want to learn more? To receive important cybersecurity updates on the latest threats with tips on how to stay safe click on this button to follow us on LinkedIn or join our critical updates mailing list.
Ask an expert
If you have a question about one of our blog posts or cybersecurity in general, our experts are happy to help.
 Cisco Talos Blog
Cisco Talos Blog
- Gamaredon campaign abuses LNK files to distribute Remcos backdoor
- Money Laundering 101, and why Joe is worried
- Tomorrow, and tomorrow, and tomorrow: Information security and the Baseball Hall of Fame
- UAT-5918 targets critical infrastructure entities in Taiwan
- Miniaudio and Adobe Acrobat Reader vulnerabilities
- Patch it up: Old vulnerabilities are everyone’s problems
- Abusing with style: Leveraging cascading style sheets for evasion and tracking
- Microsoft Patch Tuesday for March 2025 — Snort rules and prominent vulnerabilities
- Who is Responsible and Does it Matter?
- Unmasking the new persistent attacks on Japan
 CISO Online
CISO Online
- Ubuntu namespace vulnerability should be addressed quickly: Expert
- Zu wenig Budget für OT-Security
- Salt Typhoon may have upgraded backdoors for efficiency and evasion
- CIO des Jahres 2025 – Wettbewerb startet
- The Trump administration made an unprecedented security mistake – you can avoid doing the same
- How to create an effective crisis communication plan
- Researchers claim their protocol can create truly random numbers on a current quantum computer
- Malicious npm packages found to create a backdoor in legitimate code
- Trotz Hinweisen: Oracle dementiert Cyberattacke
- Diese Unternehmen hat es schon erwischt
 Krebs On Security
Krebs On Security
- How Each Pillar of the 1st Amendment is Under Attack
- When Getting Phished Puts You in Mortal Danger
- Arrests in Tap-to-Pay Scheme Powered by Phishing
- DOGE to Fired CISA Staff: Email Us Your Personal Data
- ClickFix: How to Infect Your PC in Three Easy Steps
- Microsoft: 6 Zero-Days in March 2025 Patch Tuesday
- Alleged Co-Founder of Garantex Arrested in India
- Feds Link $150M Cyberheist to 2022 LastPass Hacks
- Who is the DOGE and X Technician Branden Spikes?
- Notorious Malware, Spam Host “Prospero” Moves to Kaspersky Lab
 The Hacker News
The Hacker News
- RESURGE Malware Exploits Ivanti Flaw with Rootkit and Web Shell Features
- New Android Trojan Crocodilus Abuses Accessibility to Steal Banking and Crypto Credentials
- BlackLock Ransomware Exposed After Researchers Exploit Leak Site Vulnerability
- Researchers Uncover 46 Critical Flaws in Solar Inverters From Sungrow, Growatt, and SMA
- CoffeeLoader Uses GPU-Based Armoury Packer to Evade EDR and Antivirus Detection
- Product Walkthrough: How Datto BCDR Delivers Unstoppable Business Continuity
- PJobRAT Malware Campaign Targeted Taiwanese Users via Fake Chat Apps
- Nine-Year-Old npm Packages Hijacked to Exfiltrate API Keys via Obfuscated Scripts
- Mozilla Patches Critical Firefox Bug Similar to Chrome’s Recent Zero-Day Vulnerability
- New Morphing Meerkat Phishing Kit Mimics 114 Brands Using Victims’ DNS Email Records


