Akouto's white label managed cyber security solution provides advanced protection against online threats and security breaches to prevent financial loss caused by viruses and malware, ransomware & extortion, unplanned downtime and data corruption. Our Managed Security service partners are armed with the expertise, technology and personnel needed to defend businesses against constantly changing threats and attacks.
Technology + Expertise
Our solution protects against inbound threats, prevents users from accessing malicious sites and helps identify systems infected by the latest malware able to bypass and hide from anti-virus. Systems are actively monitored using automated analytics and real cybersecurity experts to identify threats and troubleshoot problems.Easy to deploy and manage
Our solution is inserted at the network edge with no configuration changes needed to existing routers or firewalls. The solution is centrally monitored by cybersecurity experts who assess threat information and guide IT personnel to quickly contain and resolve issues to keep your business up and running.Save time and money
Getting security right takes time and expertise. Getting it wrong is easy and can result in costly breaches, ransomware and lost revenue due to unplanned downtime. Our cybersecurity solution and experts solve this problem by taking on the cybercriminals allowing you and your staff to focus on the projects and activities that drive your business.Features
| Network Security Appliance | ✔ | Stop threats at the network level and protect all your devices including servers, desktops, laptops, mobile phones, tablets, servers, and surveillance cameras. |
| Inbound Intrusion Prevention | ✔ | Inspect all inbound network traffic to detect and stop threats from the Internet attempting to get into your network. |
| Outbound Intrusion Prevention | ✔ | Inspect all outbound network traffic to prevent users from accessing malicious content on the internet and detect suspicious activity on your network. |
| Country-based blocking | ✔ | Customize firewall rules to allow or deny traffic from specific locations. |
| Malicious IP address ruleset | ✔ | Custom malicious IP list blocks network traffic to and from known malicious IP addresses to protect all your devices from known hostile systems. |
| Intrusion Prevention ruleset | ✔ | Custom Intrusion Prevention rules inspect all network traffic to detect and prevent threats at the network level. |
| External Network Scanning | ✔ | External network scans detect open ports that may allow hackers access to your network or the systems connected to it. |
| Honeypot | ✔ | Detect viruses and other threats attempting to spread to other systems on the network. |
| DNS Firewall | ✔ | Block access to known malicious domains and URLs that are used to spread ransomware, trojans and other malware. |
| Live Monitoring | ✔ | Monitored by trained cybersecurity experts to detect malicious activity and alert your IT staff to critical security issues. |
How does it work?
An Inline Intrusion Prevention Security Appliance
The Network Security appliance blocks inbound threats and prevents users from accessing malicious sites and content. It also helps identify internal systems that are infected with malware that is able to bypass anti-virus.
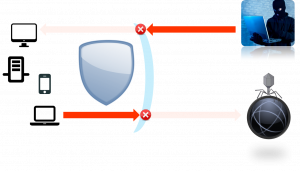
Advanced Cloud Analytics Algorithms
Advanced algorithms analyse security information to detect hidden issues and alert monitoring staff about any issues that require immediate attention.
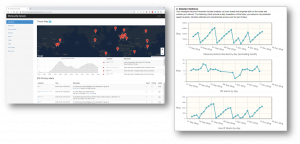
Branded Web Management Portal
Administrator and end-user portals branded with your company logo provide security information, statistics, reports, remote monitoring and management.
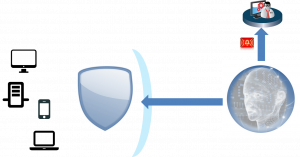
A Professionally Monitored Security Service
Security information is streamed to the monitoring servers where trained cybersecurity experts monitor and analyse the information to identify issues and work with your IT staff to contain and mitigate threats.
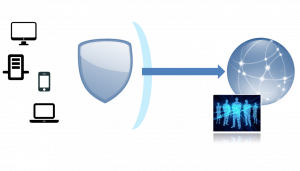
Cloud Network Scanners
Cloud-based network scanners check customer networks for unauthorized entry points and firewall mis-configurations.
FEATURES & BENEFITS
Mature industry leading security appliance provides advanced cybersecurity features traditionally only used by large enterprises.
Benefit: Protect your business with Enterprise grade security at a small business price point.
Appliance software versions and patches are actively monitored to ensure your systems are always up to date with the latest security patches and features.
Benefit: Prevent obsolete or vulnerable software and eliminate one of the primary causes of security breaches.
Intrusion Prevention inspects all inbound and outbound traffic to protect against known and emerging cyber security threats.
Benefit: Detect and block malicious activity outside and inside your network.
Cloud services and security experts monitor your systems. Automatic SMS and Email alerts enable rapid response to critical security events.
Benefit: Quickly respond to critical issues and threats and minimize the impact of potential security breaches.
Advanced firewall rules restrict traffic to and from specific countries, reducing unnecessary exposure to remote threats.
Benefit: Reduce risk by limiting the locations from which your systems can be accessed.
Cloud security scanners check external access to your network, protecting it from unauthorized access due to incorrect security policies or configuration errors.
Benefit: Prevent breaches caused by human error and common firewall misconfigurations.
